Content warning: Because of the nature of some of the activities we discovered, this series of articles contains content that some readers may find upsetting. This includes profanity and references to drugs, drug addiction, gambling, pornography, violence, arson, and sex work. These references are textual only and do not include images or videos.
Following on from the first chapters of our investigation into what cybercriminals do with their profits, we now examine various forms of business and income generation that are, in threat-actor parlance, ‘grey’ (on the boundaries of legality, and/or of questionable ethics and morality).
We acknowledge that legality can vary depending on jurisdiction. However, the breadth and depth of these activities are such that we have to categorize them somehow, and using the threat actors’ own categories is a logical if imperfect choice.
Key findings of Part 3
- We observed threat actors discussing a wide variety of ‘grey’ business interests on cybercrime forums
- Several of these – including selling spyware and vulnerabilities – may be of concern to the security industry
- Other business interests in this category include traffic generation, pornography, gambling, pharmaceuticals, import and export, drop-shipping, and selling antiques
- Other schemes of note include a proposal to outsource software development to Russian prison inmates, residency permits, and selling intelligence
- In some cases, forum discussions revealed information and images that could potentially be used to track, geolocate, and/or identify threat actors.
‘Legal’ malware and cybersecurity services
Spyware
A user proposed “legally” selling spyware to “pentesters and expensive corporations” and asked “if there are loopholes.” Other users noted that “lawyers…are needed” but that “somehow Cobalt [Strike] and others exist.” Other commenters cited FinFisher and NSO Group, and advised the threat actor to contact a lawyer.
Figure 1: A threat actor asks whether it is possible to “legally sell” malware to “pentesters and expensive corporations”
Vulnerabilities
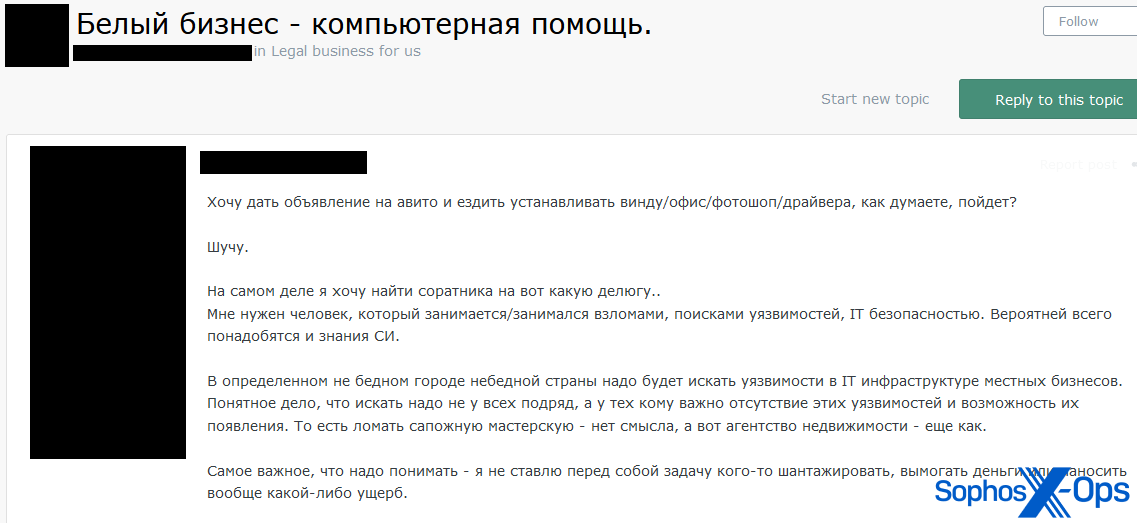
A user posted a thread looking for “a comrade-in-arms” who is “involved in hacking, searching for vulnerabilities, and IT security.” The user, purportedly based in Moscow, explained that they intended to find vulnerabilities in local businesses’ networks, contact them, provide evidence, “and provide one-time services to put the infrastructure in order or take on ongoing maintenance…our goal is to provide protection services and not to extort money.” The threat actor also mentioned that “I do not set myself the task of blackmailing anyone, extorting money, or causing any damage at all.”
Figure 2: A threat actor seeks a business partner for a vulnerability business
The user claimed that “I accidentally found myself in this situation, raised a lot of money, and got a regular client,” suggesting that the business is already up and running.
Other users noted that “there is nothing white about this, ordinary blackmail…same as how it’s good to beat someone up on the street, and then offer him your karate class.”
Traffic generation
We noted several instances of schemes relating to artificial inflation of traffic, either relating to internet advertising, or to laundering/generating money. Schemes included:
- A user who was receiving $10,000-20,000 passive profit from spending $3,000-4,000 on “adverts on popular forums and mails to corps”
- A plan to artificially inflate Spotify streams to generate revenue
- A plan to drive traffic to OnlyFans profiles
- “Lead generation” using Facebook
- Registering Telegram accounts “using a bug” to generate passive income of 20,000-500,000 rubles a day)
- TikTok promotions related to affiliate marketing.
Figure 3: Part of a detailed guide on a method for artificially inflating Spotify streaming revenue; the threat actor claimed to have “more or less successfully mastered it and, one might say, refined it” after finding it “on another forum six months ago”
We also saw a proposal to set up a marketing/advertising agency on a Tor hidden service. While the proposer did not make the nature of this agency or its clientele clear, they did refer to “your own service in a dark theme.” This could indicate that the agency would be intended to promote illicit businesses, particularly those on hidden services.
Pornography
Webcam studios
We observed an investment opportunity (ROI: refund of deposit plus 25% of profits) to help scale up a webcam studio. The threat actor outlined the costs, explained how advertising would work, and stated that the output will be “English for Western audiences.”
Another webcam studio proposal was from a threat actor who had “5-6 rooms…looking for a franchise or business plans…with approximate calculations.” Some users debated the legality of this (“I read several articles and judicial practice under Article 242 of the Criminal Code of the Russian Federation. It seems difficult to prosecute her for this activity”) and advised speaking to lawyers. Others gave specific advice on how to sign up for affiliate programs for advertising.
Figure 4: A threat actor seeks franchise or business plans “for opening webcam studios”
OnlyFans
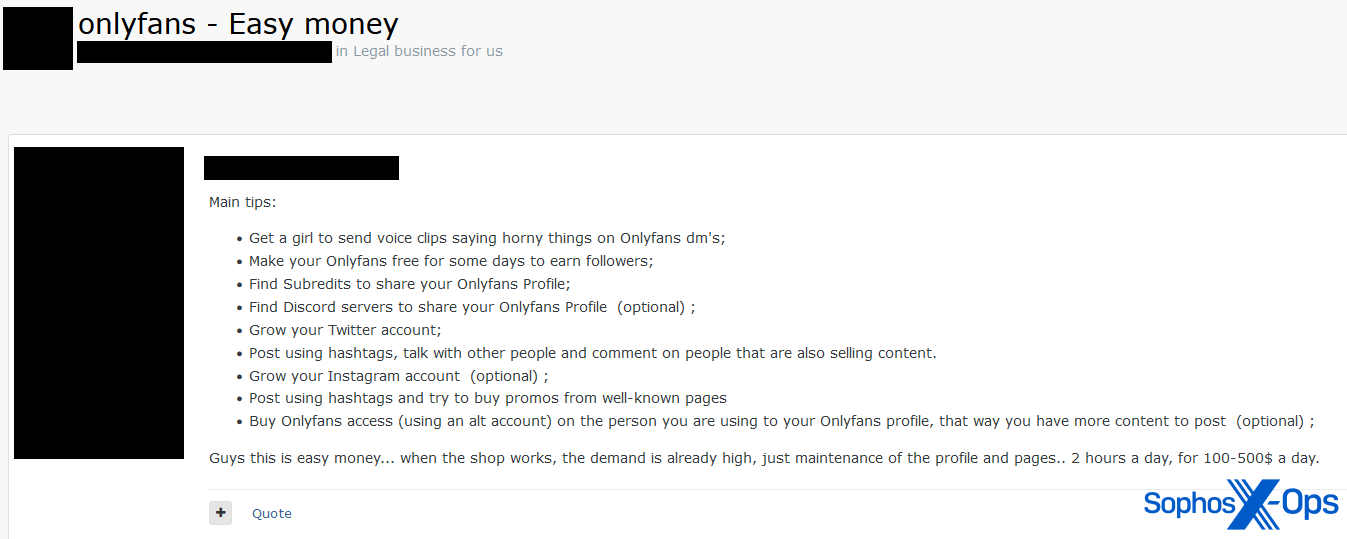
We observed multiple threads on laundering money/diversifying via OnlyFans. Some were focused on low-level laundering and cashing out (“create an OnlyFans account where you upload AI-generated foot fetish porn…you can start buying subscriptions using your stolen credit cards/PayPal accounts”); others on making a profit.
Figure 5: A threat actor outlines a scheme for making “easy money” with OnlyFans
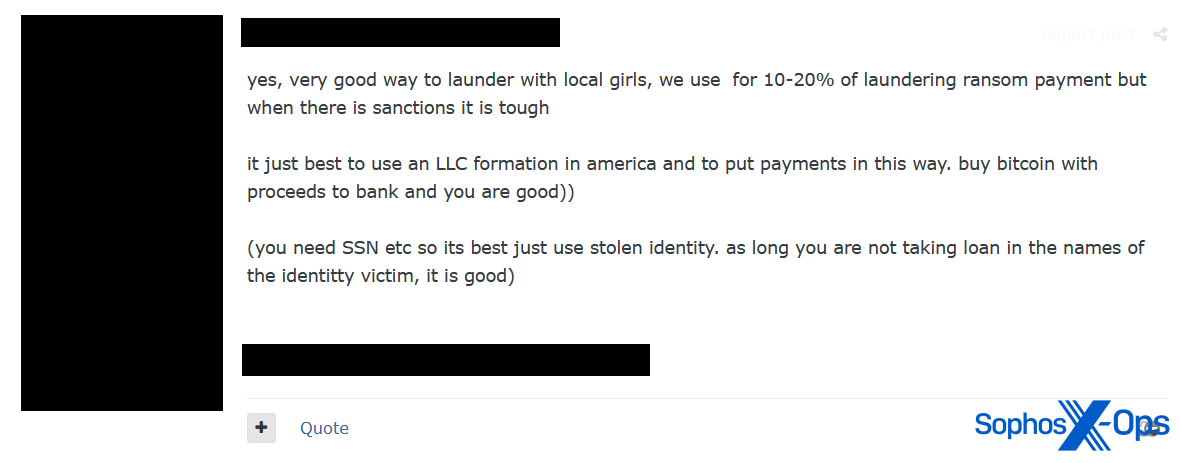
We also noted one threat actor, likely a ransomware affiliate, who noted that OnlyFans is a “very good way to launder with local girls, we use for 10-20% of laundering ransom payment but when there is sanctions it is tough…best to use an LLC formation in America…buy bitcoin with proceeds to bank and you are good.”
Figure 6: A threat actor (possibly linked to ransomware) suggests using “local girls” for laundering money
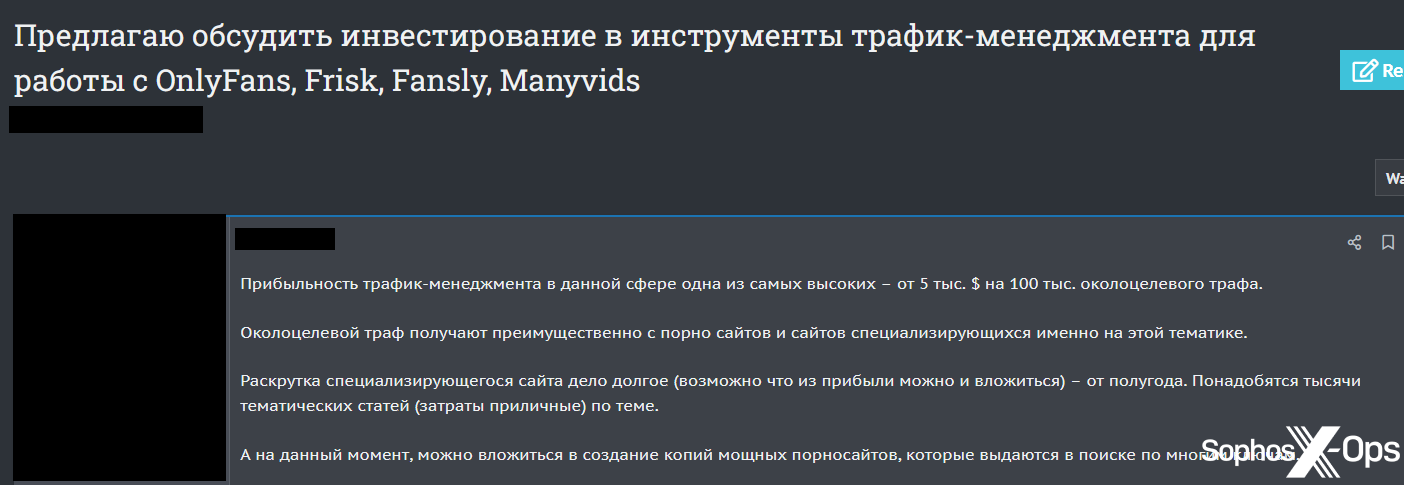
We observed a detailed proposal about “traffic management” for OnlyFans, Frisk, Fansly, and ManyVids, suggesting “creating copies of powerful porn sites that appear in searches for many keywords.” The post outlined the cost, promotional activities, estimated traffic per day, and more.
Figure 7: Part of a detailed proposal for “investing in traffic management tools for working with OnlyFans, Frisk, Fansly, Manyvids”
‘Camming’
We found a lengthy thread by a user on how they made $2,000 a month “ewhoring” for several years. This included how to deal with gift cards and gifts, how to hide your address from customers, how to make appealing content, tips on reselling content from other models, and how to attract and retain customers.
Figure 8: Part of a detailed post in which a user shares their experience of “ewhoring”
Profiting from pornography
We noted a long discussion about profiting from pornography. This included:
- Advice on how to recruit actors
- Advice on contracts
- Explicit discussions about how “shooting pornography is not a particularly pleasant process”
- Discussions on legality, including references to “illegal methods” and niche and illegal forms of pornography, including bestiality
- An admission from a user that “we are looking for our models, registering them on existing popular webcams and getting a % of their activities”
- Detailed explanations of how affiliate programs and advertisement schemes work – including percentages, amounts, payment methods, ROI, and more.
We also observed the following comment:
Sometimes they advertise ‘an online store administrator is required. A sociable girl with knowledge of English.’ Applicants come, they are told that they will become administrators, but first they need to learn how to communicate with people via the Internet, sit in chat rooms, correspond in English, talk, blah blah blah, they are put in front of computers and for about a month they are trampled and they lead to the fact that there is no store, and they have to be porn models. Some people learn about this and leave, while others stay.
Some of this information may be the result of insider knowledge; one user noted that they “had talked to the models of this studio, and they told me.”
Gambling
Investment proposals
We saw several gambling-related investment proposals, including:
- A website dedicated to betting on the NBA for residents of the US and China
- A proposal to develop a poker bot similar to the Pluribus AI bot
- An investment opportunity (ROI: 50%) to “build and launch a large-scale Bitcoin P2P betting platform.” As a bonus, the user noted that the forum community would perform pentesting on the platform.
Figure 9: A threat actor seeks investment for their “large scale bitcoin P2P betting platform”
A cryptocurrency lottery
One threat actor shared their experiences of participating in the moonpot.com lottery (where users deposit cryptocurrency into a savings pot, earn interest, and are entered into a prize draw), noting that it is “like yield farming.” They had won around $2000 so far, and sought other users to add funds to increase their chances of winning (“In case you…are afraid that I will run away with your money, I’m ready to make a deposit on the forum equal to your transfer”). The user included a screenshot showing the exact amount they won on a specific date.
Figure 10: In a thread explaining a cryptocurrency lottery, a threat actor posts a screenshot showing the money they won on a specific date
Pharmaceuticals
A threat actor noted that “there are various affiliate programs for selling pharmaceuticals in Europe and the US.” They expressed a desire “to open my own warehouse in the EU” and asked for advice on jurisdictions, pitfalls, “how quickly will the cops react…after all, this is the sale of pharmaceuticals without prescription,” and which payment gateway/bank to use.
Figure 11: A threat actor asks their peers various, specific questions on “affiliate programs for selling pharmaceuticals in Europe and the US”
Another user noted that “you can easily transfer pharma from Russia to EU,” and that “cops are not particularly interested in the activities of pharmaceutical hucksters.” This user also stated that “an acquaintance even ordered Xanax from the Czech republic to the Russian Federation.”
Figure 12: In the same thread, other users debate pros, cons, and potential pitfalls
We also observed a vague offer to sell “sports chemicals” (possibly steroids/enhancement drugs) wholesale.
Import and export
Vehicles
We observed two threads on the import/export of vehicles: First, a user offered to “bypass customs clearance” and ship 5-10 cars per week from Europe “at European prices + my interest.”
Second, a threat actor offered “clean supercars/luxury cars…for sale in the US for 50%…with full legal documents and certificates of ownership. The cars can be used for reselling/exporting/personal use.”
Figure 13: A threat actor offers “clean supercars” for sale in the US
Goods
A threat actor was interested in getting involved in the “Tajik network of Chinese goods” – “cheap Chinese clothes, shoes and accessories with a markup of 200-400%,” a scheme which is “ruled by the Tajik diaspora.” Other users suggested talking to “drop-shippers” (third-party order fulfilment specialists). One stated “I know where to get counterfeits from different brands…if you’re interested, write to me in PM.”
Another user said: “I was once closely associated with this” and provided extensive, specific details on locations, costs, and how the process works.
Unusual schemes
We saw some unusual import/export businesses, including antique Japanese katanas for sale. The user stated that “scanned copies of certificates and photographs” can be sent on request, “but only if you are really ready to purchase.” The user listed six swords, including one from the 15th century. “Everything is confidential, buyer anonymity guaranteed.” The provenance of the swords was unclear. (It’s worth noting that art and antiquities may be attractive propositions for money laundering, particularly given that some well-known auction houses accept cryptocurrency at selected auctions).
Figure 14: A threat actor lists the various antique Japanese katana swords they have for sale
We also noted the following rather cryptic post in another thread: “I am looking for a person/company to transport goods from Russia to Turkey. Not drugs and not people!”
Miscellaneous schemes
License plates
We found an investment opportunity in a car license-plate production outfit “in accordance with all the requirements of the traffic police!” Opportunities included a joint share, or a franchise (“I will provide a website, a marketing plan, advertising material, accompanying documentation, equipment, and resolution of any issues with the government. Business entry from $20,000”).
Intelligence
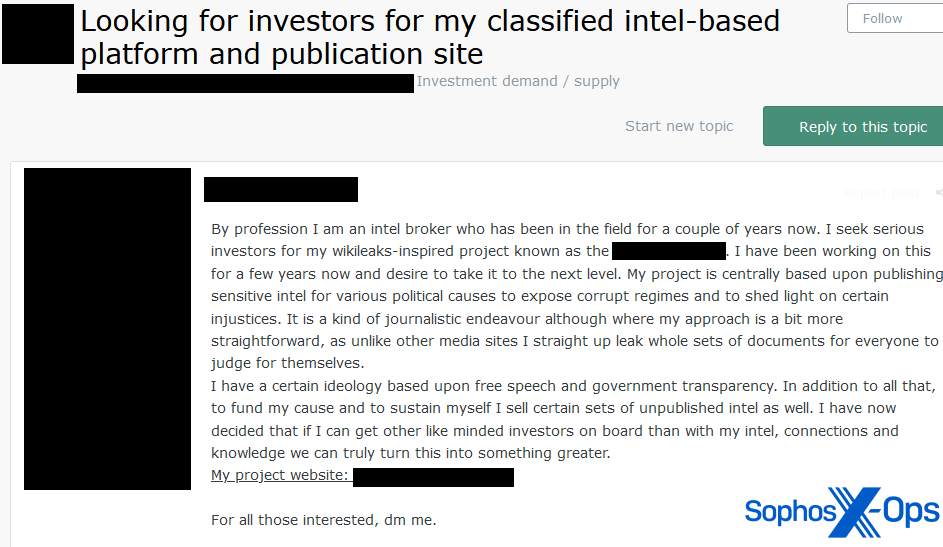
We observed an investment opportunity from a known threat actor who claims to be an “intel broker.” The project is “WikiLeaks-inspired” with the aim of “publishing sensitive intel for various political causes to expose corrupt regimes and to shed light on certain injustices…in addition to all that, to fund my cause and to sustain myself I sell certain sets of unpublished intel as well.”
Figure 15: A threat actor seeks investment for their “Wikileaks-inspired project”
Another threat actor claimed to have “several secrets ready to sell” about the Colonial Pipeline attack in 2021, including “very dark things about corruption with politicians…everything is in documents and screenshots…I ask for this information: 15,000 USD in XMR.”
Prison inmates
We noted one unconventional proposal from a prominent forum user who claimed to be involved in a variety of ‘white’ and ‘grey’ businesses, including construction and real estate. The idea was to outsource software development, hardware manufacturing, and cybersecurity to Russian prison inmates.
This proposal met with some derision (including from one threat actor we suspect from unrelated investigations to be a malware developer), but others suggested that it could work in some cases (e.g., writing crude malware).
Figure 16: A threat actor proposes using prison inmates for “software, information security, gadgets, design”
Interestingly, considering that many forum users use ‘fenya’ (a dialect popular in Russian prisons), some were disparaging about prisoners in this thread. While some users could see merit in the proposal, others thought it would be unfeasible (we noted similarly split reactions to ideas by this same user in other threads).
In this thread, users uploaded three photos of what were purportedly the interiors of Russian correctional facilities. We were able to find two of the photos elsewhere on open source, although the provenance of another was unclear.
Figure 17: An image uploaded by a forum user, possibly showing a room in a Russian correctional facility
Project management
We observed an advert from a “project manager with extensive experience in creating various black and white projects…I will help you implement your project at the best price.”
OPSEC: Who they are
During the course of our research we gained an insight into what threat actors tell others they do for a living (we noted a few threads about this across various forums). Answers included:
- Programmer
- IT specialist
- Freelancer
- Unemployed
- Internet advertising
- Sports bettor
- SEO
- Security consultant
Residence permits
We observed several users offering to sell permanent and temporary residence permits and citizenship for various countries, including Poland, Slovakia, Belgium, Portugal, Ireland, UK, Bulgaria, Romania, Greece, USA, UAE, Cyprus, Malta, and more.
Figure 18: A threat actor offers various residence permits for sale
In Part Four of this series, we’ll discuss the outright criminal (“black market”) business interests we observed across the five forums.