Content warning: Because of the nature of some of the activities we discovered, this series of articles contains content that some readers may find upsetting. This includes profanity and references to drugs, drug addiction, gambling, pornography, violence, arson, and sex work. These references are textual only and do not include images or videos.
You’re having a day off work. You wake up and enjoy some breakfast: toast with honey. You relax in your apartment, and go online. You see some internet ads, do a bit of shopping (perhaps ordering a pair of discounted sneakers), have a quick look on a dating site, see if there’s any new real estate in your area, think about applying for an online education course, and search for a plumber to fix that dripping tap in the kitchen. You head out to a sandwich bar for lunch and grab a coffee, before dropping off some laundry at the dry cleaners and getting the screen fixed on your mobile phone. In the evening, you visit a new restaurant with some friends, and treat yourself to an ice cream afterward, before getting a taxi home.
Every single business referenced in the above paragraph – from the honey to the taxi service – represents a business cybercriminals claim they are either already involved in, or have expressed interest in operating or investing in.
As it turns out, threat actors increasingly operate a wide and growing variety of online and brick-and-mortar businesses to launder the ill-gotten proceeds of their activity. Sophos X-Ops uncovered this information by investigating obscure areas of criminal forums dedicated to what threat actors euphemistically call ‘legal business’ – revealing crimes and businesses well outside of the cyber kill chain, beyond hacking and malware.
Through an examination of thousands of forum posts, we discovered a dark underbelly of fraud, theft, money laundering, shell companies, stolen and counterfeit goods, counterfeit currency, pornography, sex work, stocks and shares, pyramid schemes, gold, diamonds, insider trading, construction, real estate, drugs, offshore banking, money mules (people hired by launderers to physically or virtually transport/transfer money), smurfs (people hired to conduct small transactions in order to launder a larger amount), tax evasion, affiliate advertising and traffic generation, restaurants, education, wholesaling, tobacco and vaping, pharmaceuticals, gambling – and, believe it or not, cybersecurity companies and services.
Diversify or die
Just as wealthy ‘real-world’ criminals do, financially motivated threat actors appear to want to diversify, both to increase their profits and to reduce the likelihood of being disrupted if the cyber side of their operation gets taken down.
The prospect of cybercriminals insidiously integrating themselves into legitimate industries – as well as being engaged in a wide range of real-world illegal activities – has significant implications for cybersecurity, law enforcement, and wider society. Threat actors who expand into new territories and business ventures complicate investigations and draw more victims, collaborators, and innocent people – directly or indirectly – into their orbits. Operation Destabilise – the NCA-led disruption of a large Russian money laundering network with links to ransomware, drugs, and espionage – showed it’s big business. A recent report by Europol also suggests an increasing overlap between cybercrime and real-world organized crime.
However, it’s not all bad news. These forum posts also provide potentially useful information about threat actors, open new investigative avenues for law enforcement and regulators, and offer opportunities for the cybersecurity industry to collaborate with law enforcement.
In this five-part series, Sophos X-Ops explores the real-world businesses and criminal activities that threat actors are discussing on underground forums. This first article provides context and background on our investigation, and explores some of the ways in which cybercriminals launder money.
Parts 2-4 will cover threat actors’ business interests, using the same categories the threat actors do on the forums: ‘white’ for so-called ‘legitimate’ ventures; ‘grey’ for legally and ethically dubious (but not necessarily illegal) activities; and ‘black’ for criminal operations. (We acknowledge that legality can vary depending on jurisdiction. However, the breadth and depth of these activities are such that we have to categorize them somehow, and using the threat actors’ own categories is a logical if imperfect choice.)
In the fifth and final part, we’ll discuss the implications and opportunities of this niche of the cybercrime ecosystem.
Key findings of Part 1
- Some criminal forums have dedicated areas for discussing money laundering and real-world business opportunities, containing thousands of posts
- These areas form a ‘market-within-a-market’ – niche, obscure places where threat actors go beyond cybercrime and discuss where and how to invest their gains
- In some cases, these discussions involve complex, specialized methods (and tutorials) for cleaning and legitimizing illicit funds – including shell companies, offshore banking, money mules, and more
- We found examples of cybercrime and real-world crime ‘crossovers’, including exchanging stolen credit card data for drugs, and a recommendation to bribe drug addicts and unhoused people with drugs to help launder money
- Many users of these criminal forums appear to be interested in diversifying, whether that’s investing in apparently legitimate businesses or real-world crime
- These business interests span multiple countries and regions
Background
In October 2022, staff at the malware repository vx-underground interviewed a founding member of the LockBit ransomware group. In one sentence, near the end of the interview, the LockBit member admitted that they “have three restaurants in China, and two in New York.”
Were these threat actors ‘going straight?’ Or were the restaurants (assuming they existed) fronts for money laundering – or a means to generate separate, legitimate income streams?
The profitability of ransomware (and other financially motivated cybercrime) ironically creates a complicated financial problem for the criminal operations behind those profits. At the time of the law enforcement takedown of the LockBit ransomware infrastructure, for example, the gang possessed unspent bitcoins valued at more than $110 million. The ALPHV/BlackCat gang received $22 million from one ransom payment alone. And as Sophos’ 2024 State of Ransomware report indicates, ransom payments have increased significantly, with an average of $2,000,000 per payment. So – what are threat actors doing with their money?
We’d previously read case studies of known ransomware actors that suggested they were ‘living the high life‘, and were curious if this applied to the majority of financially-motivated threat actors – or if, like many wealthy criminals in other fields, they were smarter and more elusive than that.
Our investigation focuses on relatively obscure areas of five separate cybercriminal forums where threat actors discuss where and how to invest their gains, whether in legitimate business ventures, criminal enterprises, or (sometimes) both.
X-Ops summarizes the five criminal forums we investigated as follows:
- A relatively exclusive Russian-language cybercrime forum, which has been around since the mid-2000s. It is frequented by prominent threat actors, including ransomware affiliates, initial access brokers (IABs), and malware developers. Threat actors have used the forum’s dedicated “Legal Business” section to discuss money laundering, real-world crimes, and ‘legitimate’ business interests since 2006 (although it has fewer posts than more popular areas).
- A second, well-established Russian-language cybercrime forum, also frequented by prolific threat actors. Like the first, it has an area dedicated to discussing money laundering, real-world crime, and investments. This section was established in 2008 – but, curiously, there appears to be no activity until 2018.
- An English-language cybercrime forum which specializes in stolen data. This forum does not have a dedicated area for discussing money laundering or real-world crime/business; threads on these topics are scattered throughout the forum.
- A newer English-language cybercrime forum, frequented by lower-tier and less prominent threat actors. This site also has no dedicated area for discussing these topics. Instead, threads on these subjects are split between “OpSec” and “Monetization/SEO” boards.
- A large English-language criminal marketplace that supports a wide range of cyber and non-cyber criminal activity (including drugs, carding, and scammers). This forum has had a dedicated money laundering area for approximately five years.
We found and studied thousands of posts about multiple types of real-world money laundering, legal and illegal investments, and other forms of non-cyber income. In general, we found the greatest diversity and general expertise on the two Russian-language forums. In contrast, users on the two English-language cybercrime forums tended to be less knowledgeable, though this appeared to have no bearing on their interest in different income streams and ways to clean and invest illicit profits.
Figure 1: A link to the “Legal business” room on a Russian-language criminal forum. Note the explicit reference to “ways of money laundering”
The large English-language criminal marketplace was slightly different; because the forum area in question was dedicated to money laundering, we found less evidence of diversification, but a high degree of expertise and detail concerning specific methods of legalizing income – including complex, specialized tutorials.
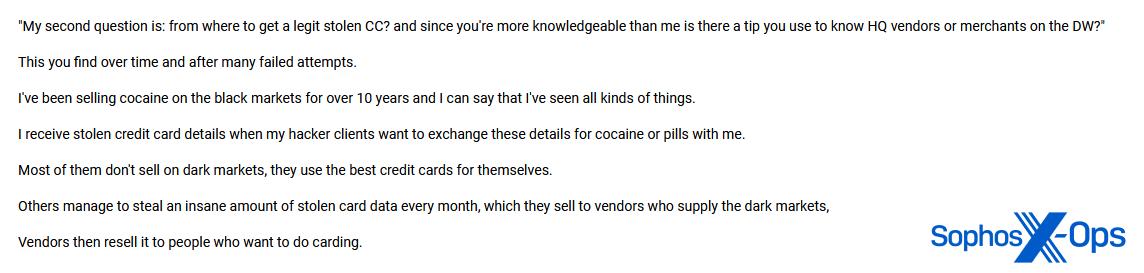
We also observed evidence on this forum of business relationships between cybercriminals and drug dealers. One example: a drug dealer reveals that carders give them stolen credit card details in exchange for cocaine and pills.
Figure 2: A criminal forum user admits to giving cocaine and pills to “hacker clients” in exchange for stolen card details
The bottom line appears to be that some financially motivated threat actors are not simply spending their money on luxury goods, or hoarding their profits, but diversifying significantly. And this diversification does not just include other crime types, but a variety of legitimate sectors and industries, as investors, stakeholders, shareholders, traders, and owners. Geographically, we observed many discussions regarding business interests and industries in Russia, as one might expect, but also in Europe, the US and Canada, Asia, the Middle East, Africa, and Australia.
While all this is, of course, concerning, it also presents some opportunities, which we’ll cover in Part Five of this series.
Cashing out, laundering, legitimizing
Our investigation focuses primarily on the diversity of legitimate and illicit business ventures that threat actors are involved in, rather than specific, technical methods of laundering cryptocurrency (such as ‘chain-hopping’ , mixing, or tumbling), or ‘cashing out.’
However, we recognize the terms ‘money laundering,’ ‘cashing out,’ and ‘legitimizing’ income streams can be confusing. For our purposes, we’ll adopt the following definitions (but note that these terms are not always mutually exclusive):
Cashing out: Realizing an illicit profit so that it can be accessed in order to launder, spend, and/or invest it. For example, a threat actor may possess illicitly obtained gift cards, credit cards, or an amount of cryptocurrency that they wish to convert to fiat currency. Cashing out does not necessarily mean that funds have been laundered or legitimized (see below definitions), as they may still be ‘tainted’ and easily linked to criminal activity.
Money laundering: A technique, online or in the real world, using cryptocurrencies or fiat currency, which is deployed to disguise the true illicit origin of funds. This could mean obfuscating the source of cryptocurrency (for example, using mixers, tumblers, or chain-hopping), or funneling funds through multiple international accounts and businesses using money mules, shell companies, etc. Laundering does not necessarily mean that the money has been legitimized (see next definition).
‘Legitimizing’ income streams: A means by which illicit income is made to appear plausible and legitimate. This may or may not be distinct from money laundering. For example, a ransomware actor may cash out, and launder, a million dollars, such that it’s very difficult – if not impossible – to trace the money back to the original ransom payment. However, if the threat actor then tries to spend that money, or use it as start-up capital, they might (depending on jurisdiction) have to account for how they acquired it, because it likely has no plausible, legitimate source. An example of legitimizing an income stream would be to set up a business using legitimate start-up capital (e.g., a loan), and then mix the laundered money with legitimate income from customers over time. This can be augmented by using smurfs (or bots, if the business is online).
As some threat actors note on the forums, financial investigators are often savvy to these activities. For example, trying to launder large amounts of money through a small physical business such as a café or salon via false reporting may raise red flags, because auditors can look at things like energy and water usage, asset inventory, footfall, etc., and determine if they measure up to the amount of reported business.
Figure 3: A criminal-forum user shares some advice on anti-laundering investigations they attribute to “a tax attorney”
While money laundering was not the focus of our research, we’ll briefly look at some interesting laundering methods, case studies, resources, and services we discovered on the forums.
Shell companies
While there are some legitimate purposes for shell companies – inactive businesses that may exist only on paper – criminals often use them for various illegal purposes, including tax evasion, fraud, and money laundering.
We observed various forum threads about shell companies. Topics ranged from basic questions (how to find someone to sign on as director/shareholder, how to use a lawyer to set up a shell company, or the best jurisdictions to create one) to more elaborate schemes:
- Setting up a shell company in North Korea
- ‘Scrubbing’ (cleaning) cryptocurrency
- Using an LLC as a “shipment front”
- Creating an anonymous LLC “for non-SEC-regulated trading…to clean XMR [Monero]” and a multi-layer structure with trusts
- Recommendations for the best jurisdictions for setting up companies (“Belize, Nevis, BVI, Bahamas…for the US you can go with Delaware, New Mexico, Nevada or Wyoming”); other recommendations included non-CRS (Common Reporting Standard) countries like “North Korea, Iran or Myanmar”; the Middle East (Dubai and the UAE appeared particularly frequently); Panama, Malta, Singapore, Estonia, and “many African nations”)
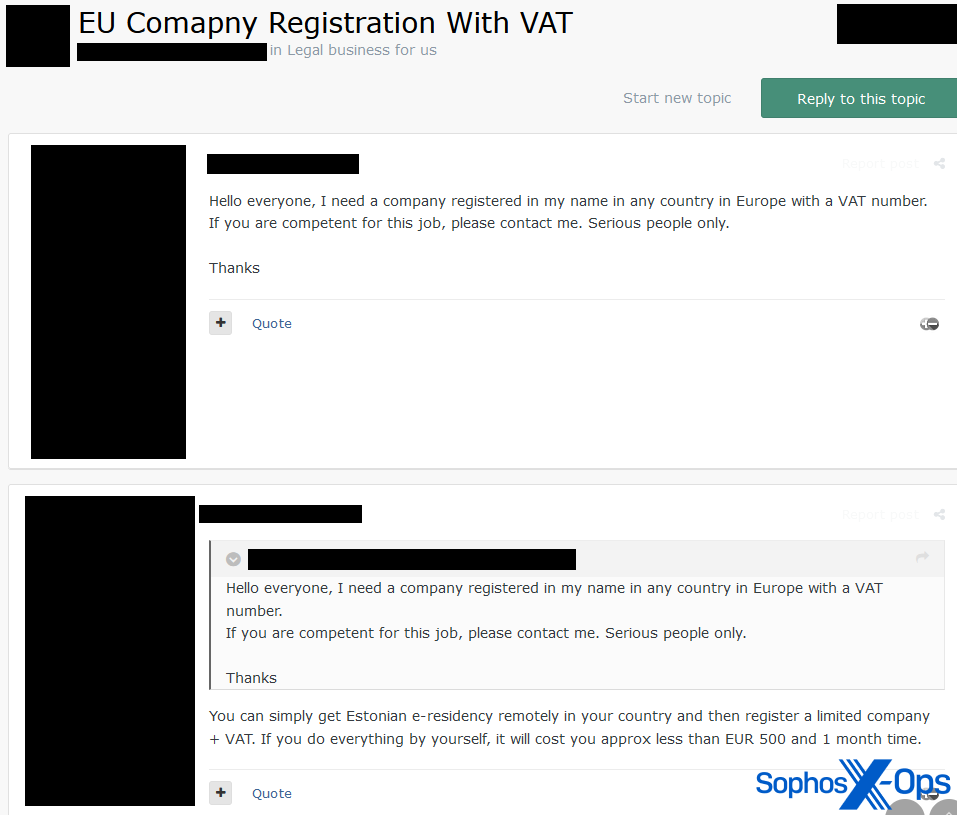
- Looking to buy a service for setting up a company in Europe with a VAT number.
Figure 4: A threat actor asks for advice on setting up an EU-based company with a VAT (value added tax) number
Figure 5: A threat actor provides guidance on setting up companies, in response to the question “would setting up an anonymous LLC for non-SEC regulated trading be a valid option to clean XMR [Monero]?”
Offshore banking
As with shell companies, people may conduct offshore banking (opening a bank account in a foreign country) for legitimate reasons, but also sometimes to facilitate crime. We saw numerous threads on offshore banking, including:
- A guide to the best tax havens
- A thread on misconceptions about offshore banking by a “no questions asked offshore and banking consultant
- A detailed guide entitled “Offshore for beginners” covering offshore jurisdictions, laws, and documentation
- Another guide entitled “Offshore mistakes,” containing common errors people make when using offshore banks.
Figure 6: A threat actor describes some “misconceptions” about tax havens and offshore banking
Mules and smurfs
Money mules are people criminals hire to receive and transfer money, sometimes using the mules’ own, legitimate bank accounts. Smurfs engage in small financial transactions on behalf of criminals that help conceal money laundering operations. Mules and smurfs may have no idea that they’re part of a criminal conspiracy.
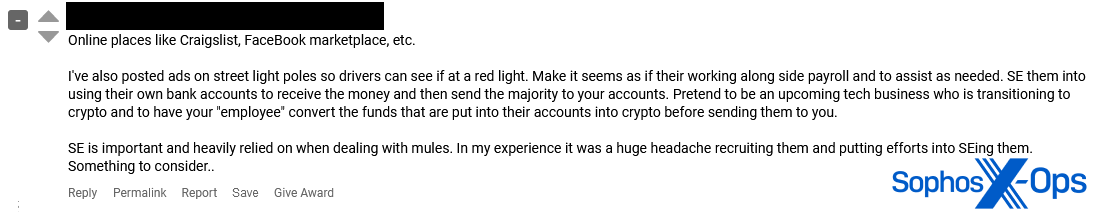
We saw several posts about mule recruitment. Among the topics were general questions about where to find mules (answers included Craigslist or Facebook Marketplace); or how to move money from one specific country to another. In one of the more complex schemes, apparently based in Finland, a threat actor sought investment in an operation involving “work[ing] with bookmaker or casino operators to farm out ruble codes 24/7 in shifts, day and night.” (As we understand it, ruble codes are a method to transfer Russian rubles from one person to another, using a cryptocurrency exchange as a middleman. Ruble codes are apparently accepted and convertible into cash by major Russian banks.)
Figure 7: A threat actor provides advice on where and how to recruit money mules
Figure 8: A threat actor seeks to recruit people “to work with bookmaker or casino operators to farm out ruble codes 24/7 in shifts”
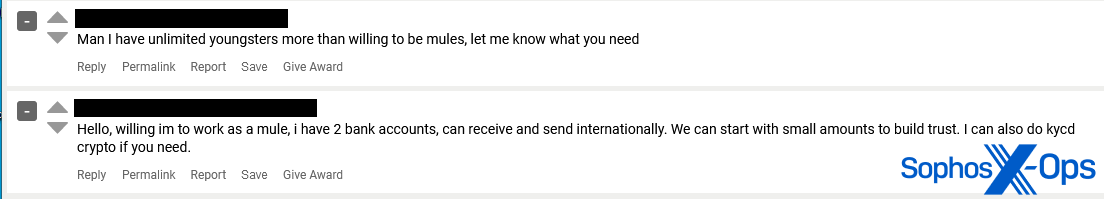
Figure 9: Two threat actors offer to help another with regards to money mules – one by supplying “unlimited youngsters” and the other by volunteering their own services
Guides and tutorials
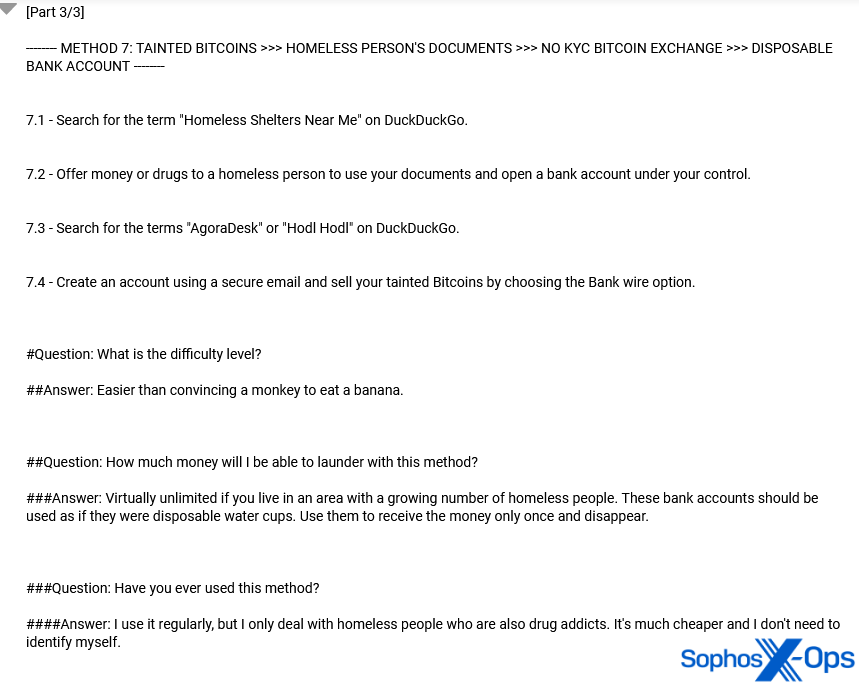
We found several guides on cashing out and money laundering, many of which were well-written, detailed, and sophisticated. These tutorials included step-by-step methods for laundering Bitcoin (written by a drug dealer who was apparently arrested a few years ago), which included the advice to “offer money or drugs to a homeless person” to open a bank account for laundering. It also included biographical information and cryptocurrency addresses to use as a virtual ‘tip jar’ for the author.
Figure 10: An excerpt from a detailed guide on various methods of money laundering (although note that this particular section appears to be focused on storage)
Figure 11: In the same thread, the OP admits to using “homeless people who are also drug addicts” for money laundering
We observed guides on how to find lawyers and accountants willing to help criminals launder money.
Figure 12: Threat actors post in a thread on how to “find the right help for legitimizing a large amount of money”
Figure 13: In another thread, threat actors advise another on “how to find a good, sketchy accountant”
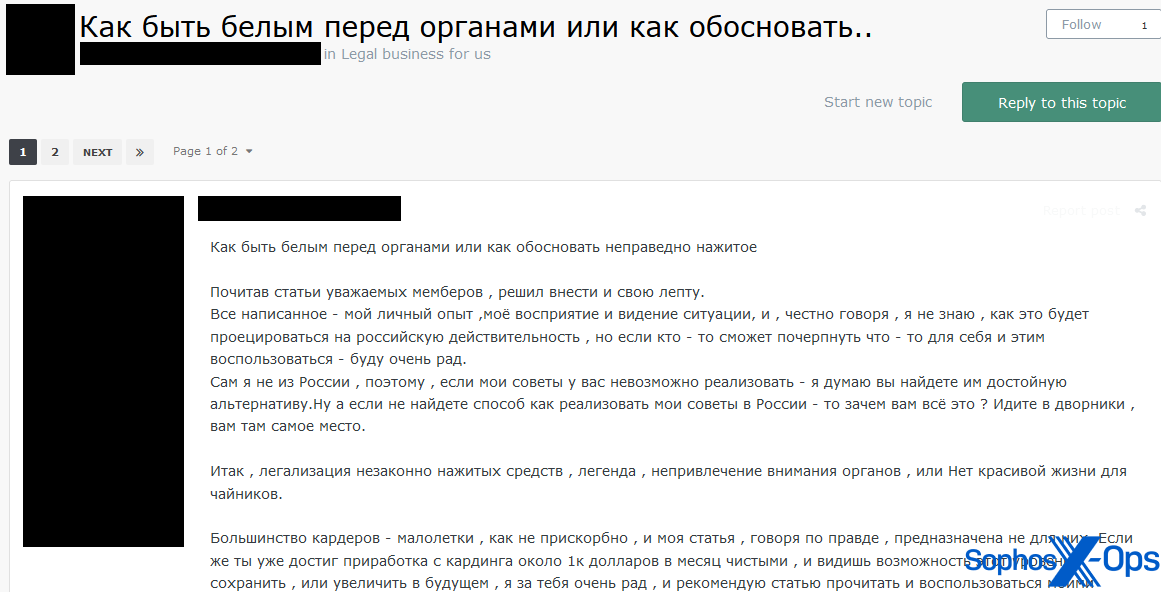
Other guides included “How to be white [i.e., appear legitimate] in front of the authorities,” containing advice on everything from offshore accounts and LLCs to spending patterns, paying taxes, not drawing attention to oneself, and the need to have a legitimate job for appearance’s sake.
The author of this guide discloses a large amount of biographical information about themselves, including their age, marital status, legitimate job, income they earned from illicit work, and a previous custodial sentence. Interestingly, we noted that the author explicitly advised readers not to party or make expensive, flashy purchases – the exact opposite behavior exhibited by some ransomware actors.
Figure 14: A threat actor posts the first part of a lengthy guide entitled “How to be white [i.e., appear legitimate] in front of the authorities or how to justify ill-gotten gains”
An unusual problem
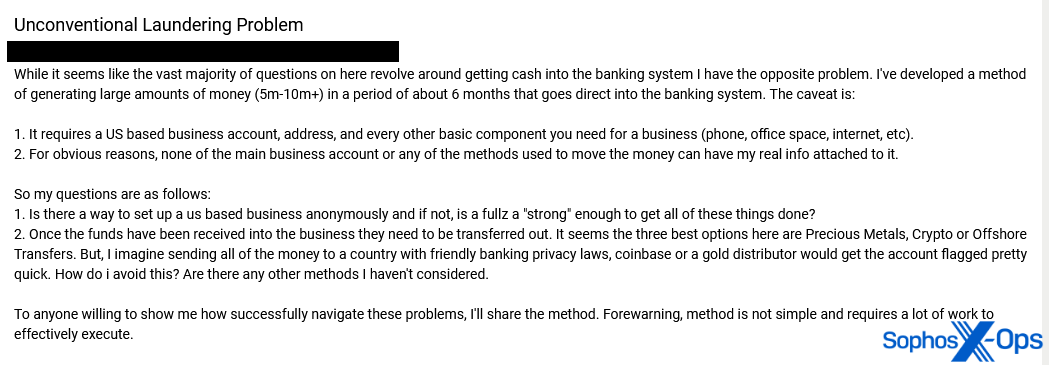
One threat actor sought advice on an unusual issue. Whereas most money laundering threads are about “getting cash into the banking system,” they had “the opposite problem. I’ve developed a method of generating large amounts of money (5m-10m+) in a period of about 6 months that goes direct into the banking system.”
This method apparently requires a US-based business account and a physical office presence. They asked for advice on the best methods of transferring money out of that business, and offered to share their method with anyone who could help them.
Figure 15: A threat actor presents an “unconventional laundering problem” on a criminal forum
Recommendations from other users included setting up businesses in Delaware, Dubai, Switzerland, or Japan; using cryptocurrency or mules; and a warning that the transfers are likely to attract attention.
On the lighter side
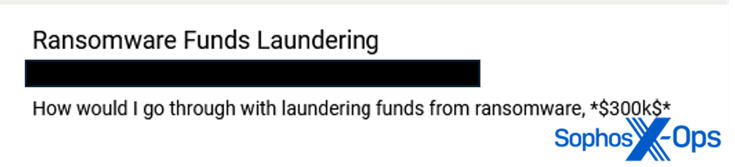
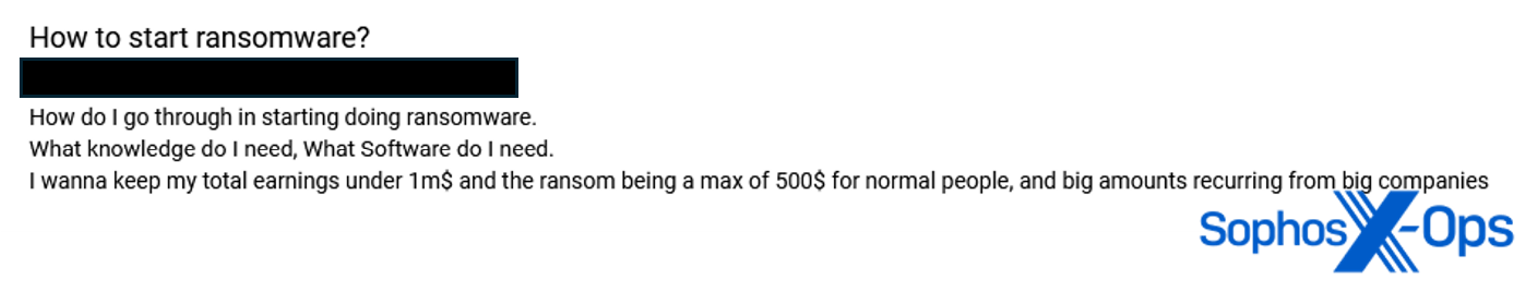
We were interested to read a post by a threat actor asking how to launder $300K from ransomware activity. We were surprised that a threat actor would be so explicit (ransomware operators are typically more discreet about this topic, at least on less private forums), so we looked at their other posts on the forum. We quickly found a thread – from around the same time as the other post – that began: “How do I go through in starting doing [sic] ransomware. What knowledge do I need, what software do I need.”
Figure 16: A threat actor asks their peers how to launder $300,000 USD from ransomware
Figure 17: The same user, at around the same time, asks their peers how to get started in ransomware
So either this user is a newbie who (in a very short time) became a successful ransomware affiliate, or they’re a newbie getting way ahead of themselves.
In Part Two of this series, we’ll look at some of the ‘legitimate’ business interests threat actors are discussing on criminal forums, before moving on to more ethically and legally dubious activities in Parts Three and Four.