Content warning: Because of the nature of some of the activities we discovered, this series of articles contains content that some readers may find upsetting. This includes profanity and references to drugs, drug addiction, gambling, pornography, violence, arson, and sex work. These references are textual only and do not include images or videos.
Following on from the third chapter of our five-part investigation into what cybercriminals do with their profits, we now examine various forms of business and income generation that are, in threat-actor parlance, ‘black’ (illegal).
We acknowledge that legality can vary depending on jurisdiction. However, the breadth and depth of these activities are such that we have to categorize them somehow, and using the threat actors’ own categories is a logical if imperfect choice.
Key findings of Part 4
- As in our previous reports, we identified a wide range of business interests in this category (outright criminal activities, dubbed ‘black’ on the forums)
- In some cases, the criminal business interests we discovered were relatively low-level: fraud, pyramid schemes, and fake goods
- However, other discussions appeared to relate to more serious criminal activity, including counterfeit gold and currency, controlling prostitution, cultivating marijuana, tax evasion, and insider trading
- We also noted that reinvesting in cybercrime may well be an attractive option for threat actors with money to spend. We saw multiple investment opportunities and proposals relating to cybercrime
- In some cases, forum discussions revealed information and images that could potentially be used to track, geolocate, and/or identify threat actors.
Fraud and theft
Bots
We observed a low-level fraud scheme involving the creation of multiple accounts to perform “tasks” under a prominent company’s rewards program. The threat actor advised using an “automation extension” to perform the tasks, and redeeming the profits as gift cards. They also provided advice on avoiding the detection of multiple accounts.
Pyramid schemes
We saw several threads relating to pyramid schemes and scams, including:
- “A remarkable technique that allows you to earn a substantial 3% interest per day on your base amount…the entire investment and withdrawal process is conducted in USDT [the Tether stablecoin]…potentially allowing you to keep your earnings without the burden of taxes”
- An investment opportunity in a pyramid scheme (i.e., to help operate the scheme, not an attempt to sucker forum users into it)
- Multiple attempts to actually sucker forum users into pyramid schemes/multilevel marketing programs – one “in the online training niche,” another that the advertiser noted was “a famous pyramid…but it really works,” and an old-fashioned get-rich-quick scheme.
Figure 1: A threat actor tries to recruit other users to an “affiliate program…[for] anyone who wants to make money selling popular educational products”
Synthetic identities
We noted multiple guides on creating ‘CPNs’ (Credit Privacy Numbers) to establish synthetic identities (sometimes known as ‘ghosts’) to apply for loans and credit cards, buy vehicles, and launder money – or to sell to people as part of fraud campaigns.
Figure 2: Part of a detailed guide on CPNs on a criminal forum
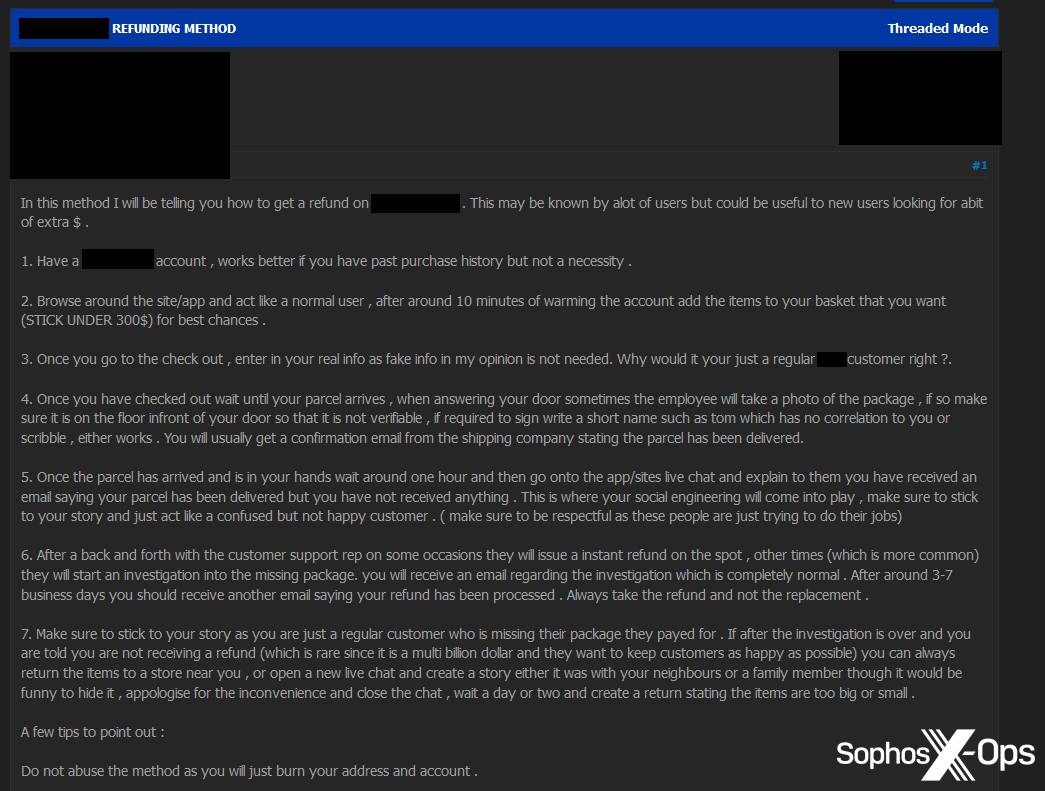
Refunds
One threat actor described a low-level scheme to fraudulently claim refunds from sports apparel companies, by claiming that deliveries did not arrive. The user outlined the scheme, providing advice on:
- How to behave on the site when ordering
- The optimal value of goods to order
- How to report the ‘failed’ delivery
- How to socially engineer customer support workers
- How to mix legitimate and fraudulent orders to avoid “burning” your address and account.
Figure 3: A threat actor outlines a low-level refund scam
Classified ads
Another threat actor provided a guide to a low-level scam on Avito (a Russian classified ads marketplace), whereby users post fraudulent listings, receive money from a buyer, but do not deliver the item and instead get the buyer banned from the platform. The post includes advice on the scheme, how to create an attractive listing, and how to set a price.
Sex work
Laundering
In a thread listing several ideas for money laundering, a threat actor suggested: “Recruit (real or fake) escorts to send you cash of your own money after they declared their ‘income’ from sex work…the prostitute idea is in the Canadian context since prostitution is legal to sell, not buy.” Another idea from the same user: “Pretend you are a hooker yourself.”
In a similar vein, a user claiming to be from Australia noted in another thread that since prostitution is legal there, they had the idea of “pretending to be an escort to clean cash.”
Figure 4: A threat actor proposes pretending to be a male escort to launder money
Controlling prostitution
A threat actor suggested creating a “job site for escort girls” – where “serious escort agencies…even brothels” can connect with “ladies who want to go to business, but there is no ticket there for the train from the village or for the plane to Dubai or anything else.”
Some users picked minor holes in this plan (competitors, difficulties in selling traffic to the site), with one arguing: “Why such a hassle, if you really want to do pussy, you make webcam studios.”
Figure 5: A threat actor proposes creating a “job site for escort girls,” sparking a long discussion about sex work
One user said: “I have the opportunity to set up my own brothel in Sochi…the Sochi cops are negotiable and won’t take very much…But you have to invest a ton.”
In the same thread, we also observed the following disturbing comment:
The girls will need to be trampled down, instilled in them with the idea that they are nobody and nothing and only under your protection can they somehow earn something. This will be especially evident in the prostitution business, where the simplest and most traditional way of controlling female employees is to make them drug dependent.
Stolen and counterfeit goods
Counterfeit gold
A threat actor sought a business partner with “an active eBay seller account” because they “have a large supply of counterfeit gold and have been selling it…the problem is…opening up new accounts.”
Figure 6: A threat actor seeks help selling “a large supply of counterfeit gold,” which they claim to have already been doing for a while
Fake goods
A threat actor sought advice on how to fake the country of origin for cheaply bought Chinese goods that they planned to sell online. Along similar lines, we noted a scheme to create an online shop and “sell high class fakes.” Other users advised them to “try to go through moderation of merch as second hand…they will not ask for invoices.” The same user provided extensive detail on their own experiences.
Ancient artifacts
In by far the most bizarre thread we discovered, a threat actor claimed to have “found some pharaonic and coptic monuments [i.e., Ancient Egyptian artifacts]…only two people know about its location. We want to sell it, but we don’t know how…to handle the shipment and the right place to sell in an auction (black market).” The user uploaded two photos of what appeared to be a sarcophagus lying on bubble wrap.
Figure 7: A threat actor claims to have “some pharaonic and coptic [sic] monuments” that they want to “sell in an auction (black market)”
Some users expressed interest in purchasing; others recommended means of verifying age/authenticity. One user claimed that they had been to Egypt for a similar job and could put the sellers in touch with a legitimate buyer “who will buy it immediately after his expert confirms.”
Drugs
Cannabis
One threat actor stated that “we have direct business relations with an American company that legally grows and sells marijuana in the US.” The user noted that the business is looking for lead generators and investors, with lead generators getting 10% of income (“income is usually $1000-$4000 per day”).
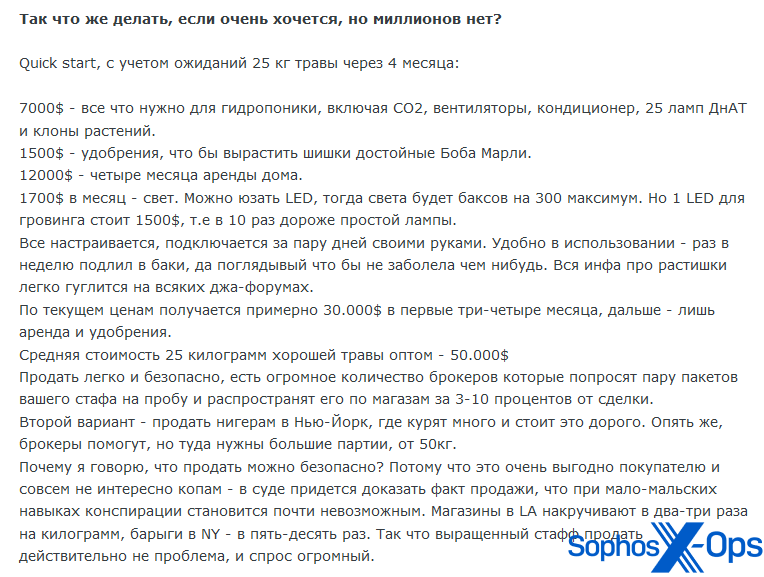
We also observed a guide on how to grow 25kg of cannabis in four months. The user outlined costs, including $7,000 for hydroponics, $1,500 for fertilizer, $12,000 to rent a house, and $1,700 a month for lighting. “The average cost of 25 kilograms of good grass wholesale is $50,000…selling is easy and safe…not at all interesting to the cops – in court you will have to prove the fact of the sale.”
Figure 8: A threat actor posts a tutorial on growing cannabis, the equipment needed, and expenditure
Drugs and carders
As noted in the first article in this series, we noted an admission from a threat actor that they have given cocaine and pills to cybercriminals, in exchange for stolen credit card details.
Figure 9: A criminal forum user admits to giving cybercriminals “cocaine or pills” in exchange for stolen credit card details
Tax evasion
We observed a detailed discussion on tax evasion methods, including specific guidance on tax evasion versus money laundering; using “a corrupt, foreign bank” versus false reporting; hiring “specialized lawyers” and more.
Figure 10: Part of a detailed discussion on tax evasion on a criminal forum
Insider trading
One threat actor claimed to have an insider in a prominent technology firm, who recommended investing big money after “the company made some major changes…they should double their stock price in 12-16 months.”
Figure 11: A threat actor claims to have an insider within a prominent technology company
Another threat actor advised others “to not gamble on the stock market…getting inside info is the only way…if hacking groups give a heads up on which company’s documents they’re going to leak you can buy put contracts on the company and profit on stock going down.”
In the same vein, another user asked about shorting stocks of companies affected by ransomware attacks, and wondered if ransomware operators have considered doing this. Most users said this was viable, although others were more doubtful (“You will attract regulatory authorities for insider trading”).
In the same thread, threat actors also discussed other types of attack (DDoS and website defacements), along with their possible impacts on stock price and whether it would be worth shorting the stock. A user suggested using SEO, deepfakes, and AI-generated articles to drive down the stock prices of attacked companies further.
On another thread, a threat actor claimed to “sell insider information well in advance of the big moves in the market for some cryptocurrencies. I usually work with investment companies, but some of you have a decent amount of cryptocurrencies, and I believe that I can be of great help to you.”
Reinvesting in cybercrime
During our research, we noted many threat actors asking their peers what they should invest their money in, and replies such as “invest it in the business that brought you this income. It’s obvious.” Reinvesting in cybercrime may be attractive to threat actors who have ‘paid their dues’ and profited – they can invest in a new project in a familiar field, and reap the rewards while being exposed to less risk.
Malware and phishing
We saw several investment opportunities in in-progress/in-development malware and campaigns, including an investment opportunity ($1,000-2,000) in an Android botnet, with the ability to steal credit card info, spam contacts, forward incoming calls, launch custom apps, and intercept incoming SMS messages. A screenshot was included.
We also noted:
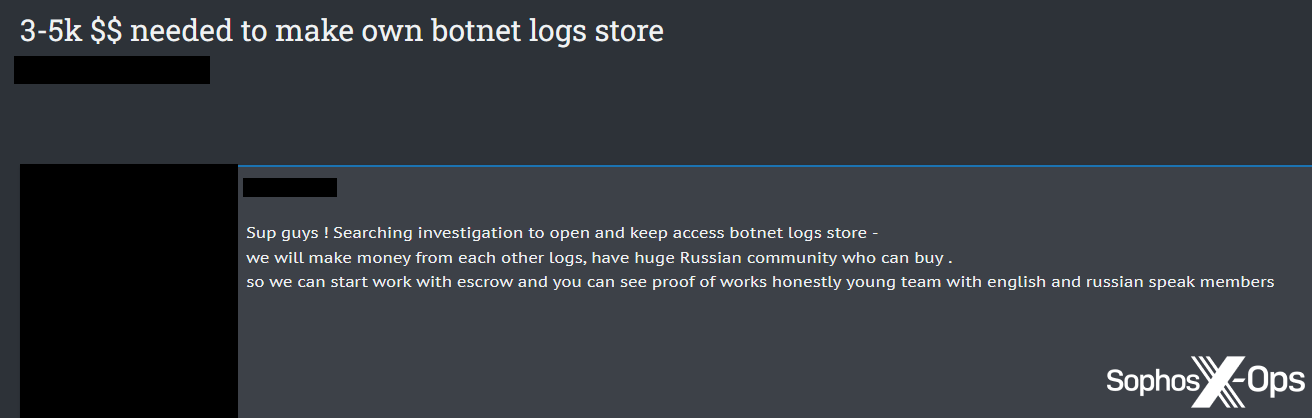
- An investment opportunity ($3,000-5,000) to open a store for botnet logs (i.e., stolen data from infostealers)
- An investment opportunity ($5,000) in a Telegram phishing tool/campaign
- A vague proposal relating to an MT103 (a protocol used in SWIFT) staging server (“I am looking for cooperation with a dark web developer…we have a deal for 10 million dollars”).
Figure 12: A threat actor seeks investment to create their own “botnet logs store”
Figure 13: A screenshot of a Telegram phishing platform, included as part of a pitch to potential investors on a criminal forum
DDoS
We saw an opportunity (ROI: 30% of profit) to invest in a year-old DDoS-related project (the user insisted that this was not a scam, pointing to their reputation and lack of arbitration complaints, and the fact that they were willing to discuss conditions privately).
SIM-swapping
We observed an investment opportunity (ROI: 20% of each cashout) in sim-swapping. “I have crypto logins and bank logins with money, my last step is sim-swapping.”
Crowdfunding
One threat actor proposed launching a crowdfunding platform on Tor “for grey/black topics.” Other users appeared to be keen in principle, but noted that the platform would need to both ensure anonymity and prevent scams. One user suggested smart contracts as a possible solution.
Figure 14: A threat actor proposes a “darknet” crowdfunding platform for criminal activities, likening the principle to Kickstarter
Counterfeit currency
A threat actor proposed a scheme whereby they would provide other users with counterfeit US currency to launder, before giving the OP a percentage. The OP suggested $400 (four $100 bills) to start, later rising to thousands. The counterfeit bills allegedly had multiple serial numbers, watermarks, security strips, optically variable ink, and passed the “pen test” (a method to detect counterfeit bills via a special ink), but did not work in ATMs and needed to be aged and treated before use.
Another user outlined a plan for counterfeit bills, and provided details on their virtual and physical OPSEC measures. The latter included:
- Never using the bills in retail stores, only at physical meet-ups (e.g., Craigslist transactions)
- Going from city to city
- Never using money for trivial things like hotels, food, gas
- Selling the illicitly acquired items in different countries
Figure 15: A threat actor goes into significant detail regarding their plan to distribute counterfeit bills
Possible assault
Finally, we observed a particularly disturbing thread, although it was (probably deliberately) very vague. A threat actor asked the cryptic question: “Has anyone encountered or perhaps heard of people being intimidated by voices? A person is mixed with some substance and then he begins to have severe problems.”
Figure 16: A threat actor posts an unusual question on a criminal forum
Another user responded:
You can use a ‘truth serum’ (scopolamine or analogues, available on the darknet)…the person himself will give up everything and tell you everything. In real life, I saw a successful robbery using scopolamine, the man did everything he was asked to do – he took the documents and laptop out of the house, he withdrew money from the ATM, he himself entered passwords in banking. Be careful about dosing.
Scopolamine (prescribed to manage, among other things, nausea and vomiting caused by motion sickness or surgical anesthesia) is known to have been used for robbery, and allegedly also to facilitate kidnappings and sexual assaults.
Over the past four articles, we’ve explored a wide array of business interests, ranging from the innocuous (digitizing VHS tapes and creating a mobile fitness app) to the downright criminal (interest in operating a brothel, counterfeit bills, growing cannabis) and pretty much everything in between. But what does this mean for the cybersecurity industry, law enforcement, and society as a whole?
In the concluding chapter of this series, we’ll examine the implications, challenges, and opportunities of threat actors moving beyond the cyber kill chain.